What is it?
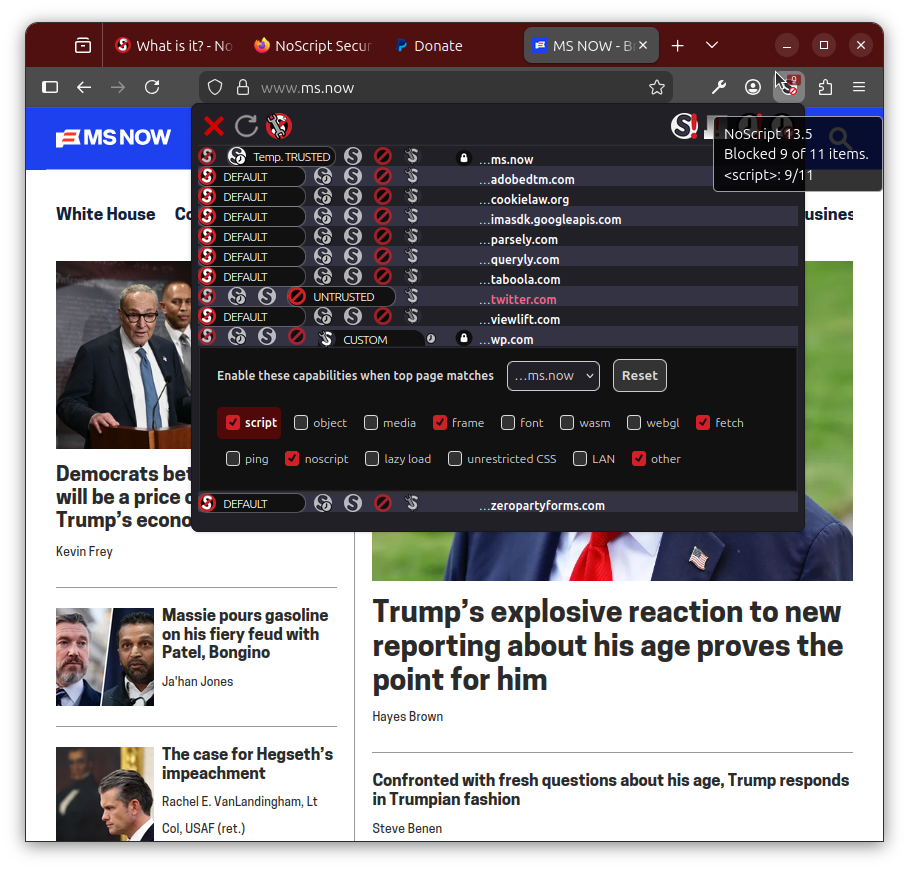
The NoScript Security Suite is Free Open Source Software (FOSS) providing extra protection for Firefox (on Android, too!), Chrome, Edge, Brave and other web browsers, by letting user decide freely which site they trust enough to run code in their browser.
NoScript enables consensual browsing: your browser, your choice!
NoScript is a built-in key security component of the Tor Browser, the top anonymity tool defending millions against surveillance and censorship.
This browser extension allows JavaScript and other potentially harmful content to be executed only by trusted web sites of your choice (e.g. your online bank).
NoScript also provides the most powerful anti-XSS protection ever available in a browser.
NoScript's unique pre-emptive script blocking approach prevents exploitation of security vulnerabilities (known, such as Meltdown or Spectre, and even not known yet!) with no functionality loss: you can enable JavaScript and other dynamic capabilities for sites you trust with a simple click.
Staying safe has never been so easy!
Experts* will agree: the web is really safer with NoScript!
* experts endorsing NoScript, among others: Edward Snowden (former NSA analyst and whistleblower against surveillance state); Window Snyder (former top security officer at Microsoft, Square, Inc., Apple, Fastly, Intel and Mozilla Corp.); Douglas Crockford (Javascript expert and creator of the JSON format); the Sans Internet Storm Center